Cisco ISE 802.1X Authentication
Before We deep dive into 802.1X authentication we should understand ISE authentication and authorization process.
Authentication is used to know who is going to access this network.
Authorization is configured to define what you can access using your identity in this network.
Authentication Methods :- Generally we used 2 types of authentication for cisco ISE in enterprise network.
MAB - Mac access bypass :- Used endpoint mac address to define authentication and authorization policies.
802.1x - Used username and password to define authentication and authorization policies.
802.1X authentication is used in enterprise were you want a user to provide his identity before he get
access to enterprise network.
Example:- You want to define policy in your office network with your Active directory or want to define different network access to different vlans in your network, Can to this with the help of ISE authorization policy.
----------------------------------------------------------------------
Configuration example for 802.1x Authentication in enterprise network.
1. NAD configuration.
2. ISE DACL configuration. ( Optional)
3. ISE Authorization profile.
4. ISE Authentication and authorization profile configuration.
----------------------------------------------------------------------
NAD Configuration.
Enable AAA and configuration Radius and aaa setting in switch.
----------------------------------------------------------------------------
aaa new-model
----------------------------------------------------------------------------
radius server ISE
address ipv4 ISE-IP auth-port 1812 acct-port 1813
key cisco
----------------------------------------------------------------------------
aaa group server radius ISE
server name ISE
----------------------------------------------------------------------------
aaa authentication login default group ISE local
aaa authentication dot1x default group ISE
aaa authorization network default group ISE
aaa accounting dot1x default start-stop group ISE
----------------------------------------------------------------------------
aaa server radius dynamic-author
client ISE-IP server-key cisco
server-key cisco
----------------------------------------------------------------------------
aaa session-id common
----------------------------------------------------------------------------
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 25 access-request include
----------------------------------------------------------------------------
configuration of switch port for dot1x and Mab authentication.
interface GigabitEthernet0/1
switchport access vlan 20
switchport mode access
negotiation auto
authentication event fail action next-method
authentication open
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
mab
dot1x pae authenticator
spanning-tree portfast edge
end
----------------------------------------------------------------------------
ISE DACL Configuration.
DACL is a dynamic Access list ISE will push to NAD to provide specific access for authentication session for users.
Every port can have different DACL and permission to network based on there authorization policies defined.
DACL Example. - In this Dacl we will deny host to some networks in our Enterprise and allow to all other networks.

----------------------------------------------------------------------------
ISE Authorization Profile
We can create different authorization policies as per our requirement and apply different DACL to each policies.
To Create DACL and authorization profiles Go to Policies -> result => Authorization => downloadable ACL and Authorization profiles.
----------------------------------------------------------------------------
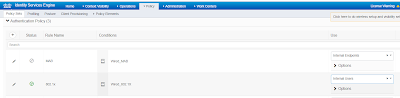
Authentication and authorization policies.
We used Simple condition in authentication and authorization policies.
Authentication Condition :- Authentication protocol should be 802.1x wired and used in from internal created users in ISE.
Authorization Policy Condition :- If user is from Employee group then apply our authorization profile.
Note :- You need to do basic wired services enable in your desktop and some basic config for 802.1x to work from laptop or desktop.
----------------------------------------------------------------------------
Thank You.
Can reach out to Me if any concerns with Cisco ISE LABs and real time projects.
Can find my contact details in my profile.




Comments
Post a Comment